We learned about the various types of smart cards and how they interact with various operating systems. The basic part we learned is that this is a very complex subject to tackle! The best way to go forward is to see a couple examples of how things can be set up.
Mac OS X 10.4 to 10.11
In these OS versions, the CDSA framework is present. Let’s start however with a couple new terms:
CCID
The CCID (chip card interface device) is a USB protocol that allows a smart card to be connected to a computer via a card reader. Obviously this is done over USB, but there are increasing Bluetooth based readers on the market.
Effectively this can be simplified down to the driver for the smart card reader.
TokenD
Taken straight from the open source “SmartCard Services” page, a TokenD is the low-level module(s) which interface to each specific Smart Card’s applet or file OS.
This is the driver that allows the computer to talk to the chip on the card.
Example Instructions
This assumes you have a properly set up AD environment with the card hash already tied to the correct user account. I’ll explain about local accounts later on. So as part of your deployment process, this is what needs to happen.
- Enable smart card authentication through the authorization database.
- sudo security authorizationdb smartcard enable
- Bind the computer to Active Directory.
- Deploy your internal certificate authority cert to the System keychain.
- A configuration profile works best for this.
- Install the CCID driver for your smart card reader.
- Install the TokenD driver for your brand of smart card.
- Deploy a profile that enables the screen saver when the token is removed.
- You may have to create your own. Tim Sutton’s mcxtoprofile is handy for this. The plist to capture is the user preference “com.apple.screensaver.plist”.
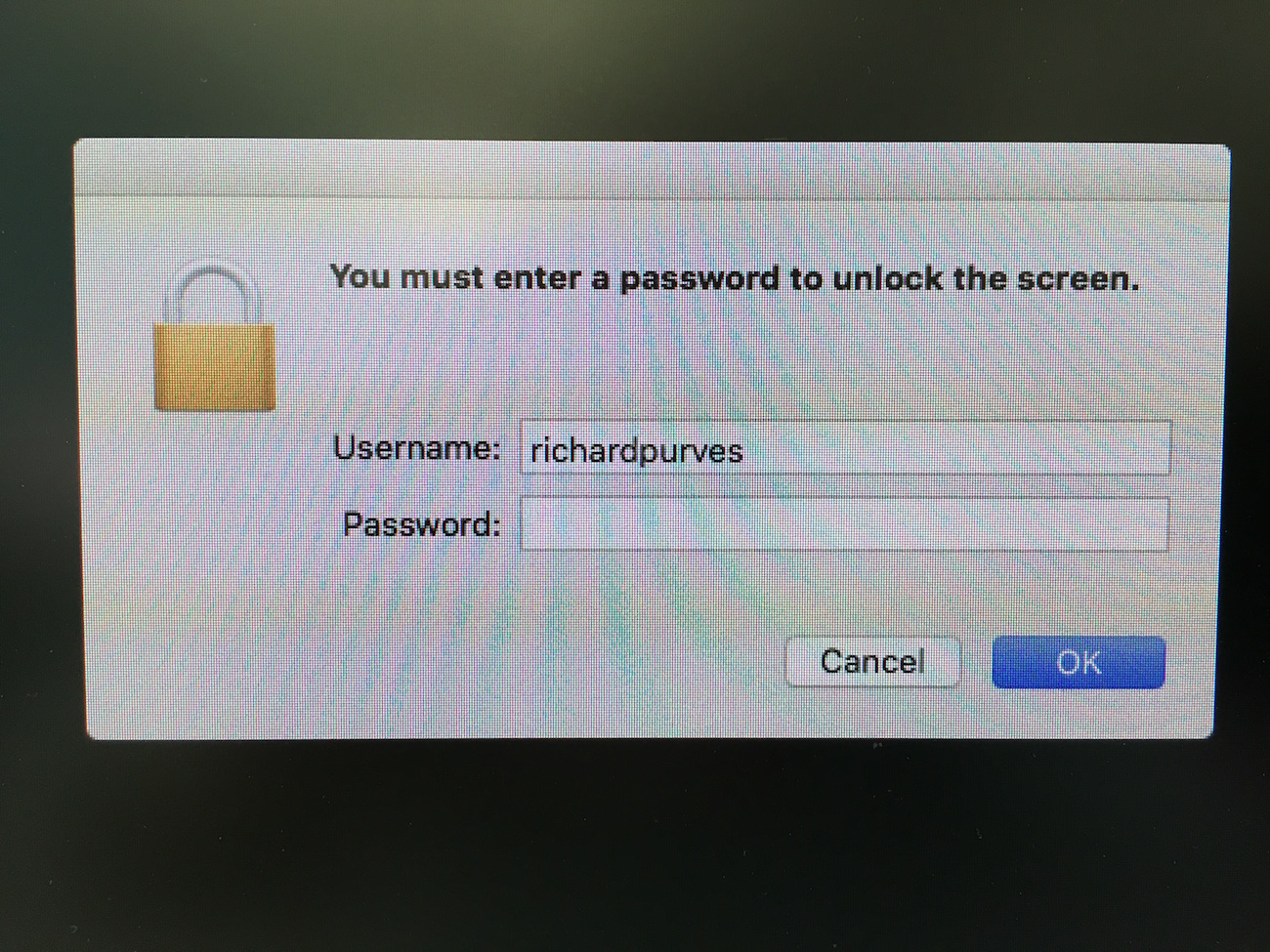
Now with any luck (and good fortune with drivers) (and smart card reader firmware), when you go back to the loginwindow it will ask for a password for a select user account. Insert your smart card, the password should change to PIN. If so, it works!
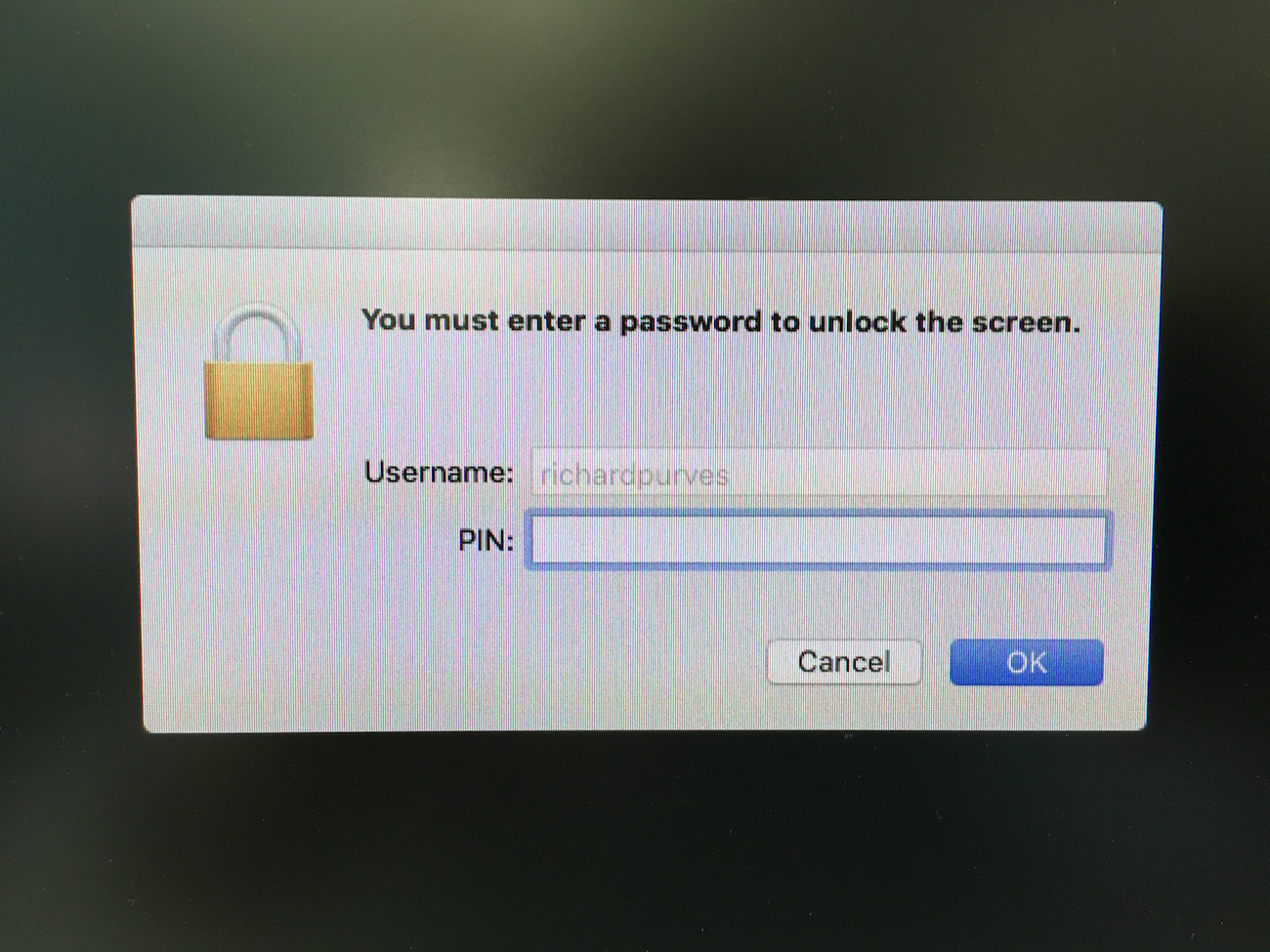
The next test is to activate the screensaver. Again it will ask for a username and password until you insert the card. Then it should auto populate the username field and change from password to PIN. Don’t forget to set your security preference to require a password on screensaver immediately!
Caveats
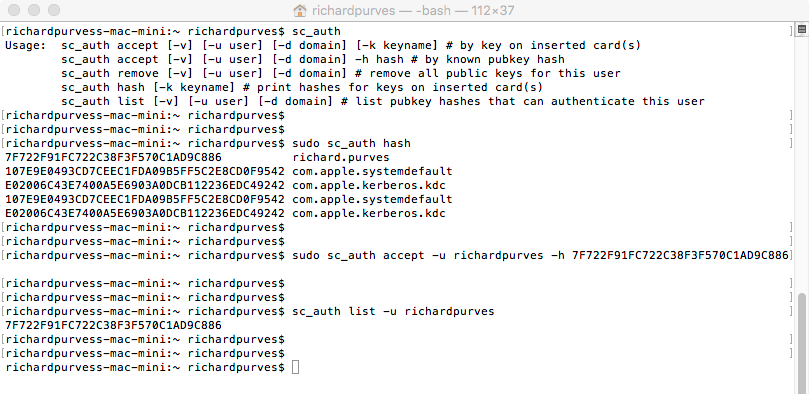
Your Active Directory service must contain the hash of the smart card in the “AuthenticationAuthority” field. You can check an account on a mac with the “sc_auth” command. An example is below.
You must deploy either a managed preference or preferably a configuration profile for the screen saver lock mentioned above. OS X 10.11.5 has a bug that continually resets this preference unless forced by preference or profile. A simple defaults write isn’t good enough and will be reset.
If a local account, the account password and the card PIN MUST MATCH. Unless this is done, if you log in with the card PIN it will fail to unlock the user account keychain. Logging in as the user will fail to unlock the card keychain. In either case, you will be prompted for a password to unlock with probably the most confusing error dialog for normal users. Best avoid.
Also if a local account, you must pair the card to the account. You can do this only via a command line process. The entire process from finding the hash to pairing the card to the account is below.
macOS Sierra onwards
This space intentionally left blank.
At the time of writing this is purely speculatory. I do not have a developer account to test the newly announced beta of this OS. However from the videos released for WWDC 2016, it is likely that the old smart card framework has been totally removed and so the method above will fail to work.
All is not lost. Apple has fully incorporated a new native API for smart cards called “CryptoTokenKit”. This still allows smart card access but at the cost of requiring totally new drivers for both card reader and card OS.
Now we just need vendor support to see this through. We wait and see.
And finally …
I’m leaving so much out here. The highly variable vendor support, finding out what kind of card you possess, the best kind of readers with cards and card drivers (hint: HID and Gemalto). The not very active but drowning in information open source websites that deal with these cards. So much to type, so little time. Here’s a set of links that I used when writing these posts and hopefully they’ll be handy for you too.
http://smartcardservices.macosforge.orghttps://github.com/OpenSC/OpenSC/wikihttp://ludovicrousseau.blogspot.chhttps://randomoracle.wordpress.com/2015/01/16/smart-card-logon-for-os-x-part-i/